Hey amazing Bug Hunter!
After many month, I decided to write writeups regarding my bounty from Google of worth $5000. So without wasting any time, lets begin the story!The Story
After getting many duplicates and N/A from H1 & Bugcrowd, I decided to write about my journey and started searching for VDP programs. I got many bugs and reported to them but till then no reply . Finally, I decided to start hunt on google.
Started searching google subdomains using Google dorks. I know its piece of a shit but never mind. I found few domains and nothing work for me. So finally, I decided to test on google cloud Acquisition.
I started searching more about the looker.com, I started searching common bugs like xss,sqli,htmli.. etc. But it didn’t work! :(
After doing a lot of search, there is a default configuration on the website page, which allows for a directory traversal bug
I got an interesting Option After explaining the attacking scenario and impact, they reopened and accepted the bug. Whooo hooo! and rewarded with $5000.Timeline:
- Jun 28, 2021 : Reported
- Jun 28, 2021 : Status: Won’t Fix (Not Reproducible)
- Jun 28, 2021 : Status: Accepted (reopened).
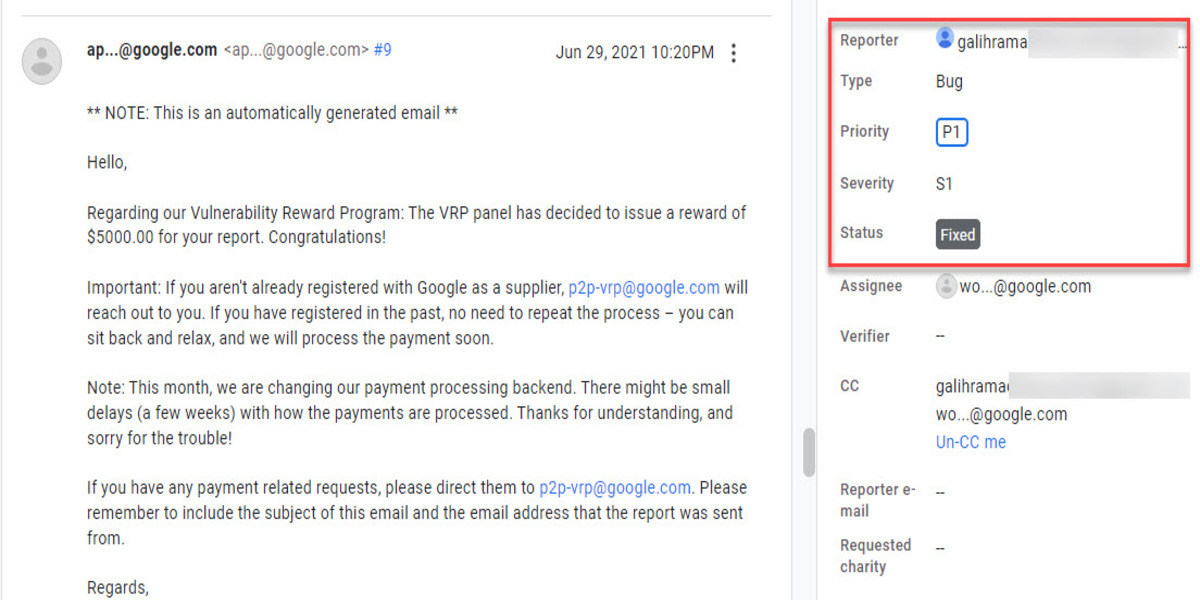
- Jun 29, 2021 : Hello,Regarding our Vulnerability Reward Program: The VRP panel has decided to issue a reward of $5000.00 for your report. Congratulations! Important: If you aren't already registered with Google as a supplier, p2p-vrp@google.com will reach out to you. If you have registered in the past, no need to repeat the process – you can sit back and relax, and we will process the payment soon. Note: This month, we are changing our payment processing backend. There might be small delays (a few weeks) with how the payments are processed. Thanks for understanding, and sorry for the trouble!If you have any payment related requests, please direct them to p2p-vrp@google.com. Please remember to include the subject of this email and the email address that the report was sent from. Regards, Google Security Bot.
- October 30, 2021 : fixed.